Risk management consultants
World-class business resilience
We are the leading specialised provider of resilience & risk management solutions throughout Australia & New Zealand. We empower clients to strengthen their resilience maturity using a practical and adaptive approach.

Business as usual as quick as possible
- Business Continuity
- Incident Management
- Crisis Management
- Crisis Communications
- Enterprise Risk Management
- CBCI Accredited Training
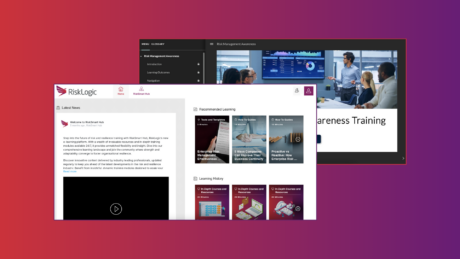
Partnered with the best software
Our partnerships allow us to provide our clients with the world’s best resilience management software solution & AI-powered risk and compliance software.

Industries We Serve
We’ve worked with 500+ organisations across 30+ industries, equipping our clients with the experience, capabilities and tools to confidently continue operations & minimise risks.
-
Education
Tertiary institutions, online learning platform providers & more.
-
Property & Retail
Retail providers, construction companies & more.
-
Finance
Banking institutions, insurance companies, brokerage firms & more.
-
Utilities & Infrastructure
Providers of electricity, natural gas, water & more.
-
Transport, Supply Chain & Aviation
Airlines, trucking, railroads, suppliers, logistics providers & more.
-
Not-for-profit
National charities, foundations, employment training & more.
-
Federal, State & Local Government
Government Departments, Statutory Authorities, Councils & more
-
Manufacturing
Electronics, automotives, clothing, food production & more.
-
Health & Aged Care
Accomodation and equipment providers, health care providers & more.
Start Building Your Resilience
We’re excited to get started working together on your resilience management. Fill out our contact form and our expert team will reach out to you shortly.